
ThreatLocker
Endpoint Security
ThreatLocker is a robust cybersecurity solution designed to protect organisations from data breaches and unauthorised access.
As an MSP, integrating ThreatLocker into our services significantly enhances our clients’ security posture. HOLKER proudly introduces Managed ThreatLocker as part of our Managed Service offering, featuring key components.
Key Features of ThreatLocker
1. ThreatLocker Protect:
- Application Control: Enforces application allowlisting and blocklisting.
- Ringfencing: Isolates applications to prevent lateral movement during attacks.
- Storage Control: Extends control to storage devices based on policies.
2. ThreatLocker Detect:
- Behaviour Monitoring: Continuously monitors endpoint behaviour.
- Real-time Alerts: Receives alerts for suspicious activities.
- Integration with ThreatLocker Protect: Comprehensive security coverage.
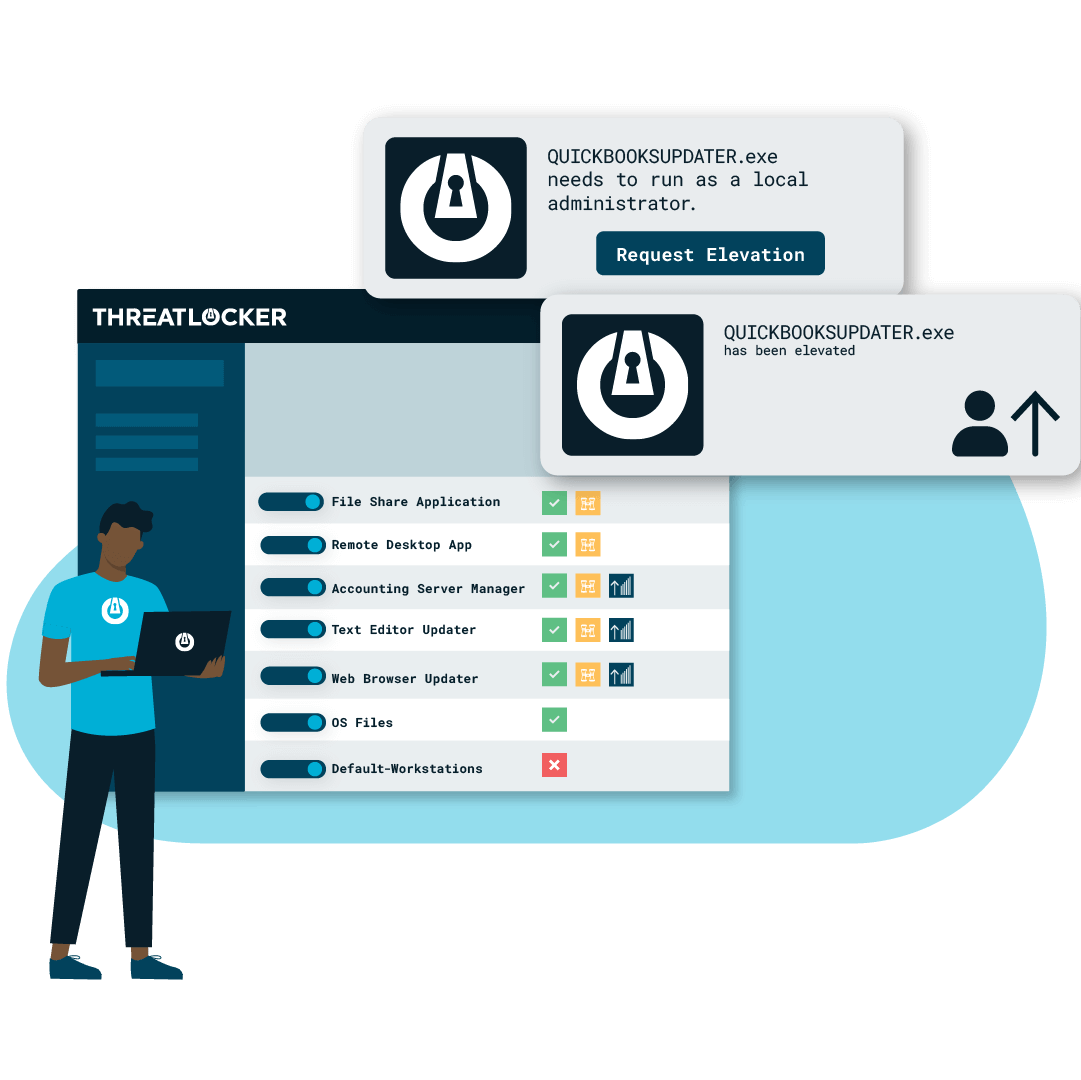
3. Elevation Control:
- Manages privilege escalation to limit unauthorised changes.
4. ThreatLocker Storage Control:
- Manages data security by restricting unauthorised storage access.
ThreatLocker® Detect is a tool that monitors and alerts on suspicious activities within your network. It can monitor Windows event logs, alert on unsuccessful login attempts, and isolate machines in response to perceived threats while allowing specific remote access for investigation.
Storage Control provides policy-driven control over storage devices, whether they are local folders, network shares, or external storage like USB drives. It allows granular policies to be set, such as blocking USB drives or controlling access to backup shares.
Yes, it logs all actions related to file movements, deletions, and the programs used, allowing you to see exactly what happened and recover lost or deleted files.
ThreatLocker® meets various security compliance standards, including HIPAA, by enforcing encryption across all devices and creating fine-grained application access controls to limit risky access.



Why Proactive Security Matters
The threat landscape evolves constantly, with cyberattacks growing more sophisticated. Data breaches are costly both financially and in terms of reputation. Proactive security measures are essential to mitigate these risks.
What is Zero Trust?
Zero Trust security model eliminates implicit trust in any one element, node, or service.
Zero Trust Architecture security model assumes that a breach is inevitable or has likely already occurred, so it constantly limits access to only what is needed. In essence, a Zero Trust Architecture allows users full access but only to the bare minimum they need to perform their jobs.


In Conclusion
With ThreatLocker, HOLKER strengthens security and ensures peace of mind for our clients. Let’s unlock a safer digital future together!
Need more information on our services?
Fill out the form and one of our colleagues will be in touch to discuss your requirements. You can also call us on 0333 305 2020 if you need a faster response.
- Talk to someone who can answer your questions.
- No hard sales, just a friendly chat.




